Overview
By default, Azure App Services will not enforce any authorization for your Web Apps. You can implement authorization within your code, or you can configure an Identity Provider to perform authentication and authorization for you. In this article, I will walk you through the process of configuring Azure Active Directory as an identity provider. This will force anyone to log in with an Account in or registered in Azure Active Directory before accessing your website.
Register Identity Provider
The first step after you create your web app is to register an Identity provider.
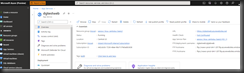
Navigate to the App Service, as shown in Fig. 1.
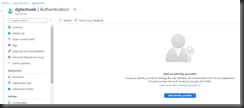
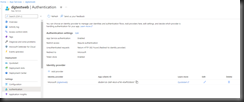
Select "Authentication" from the left menu to open the Authentication blade, as shown in Fig. 2.
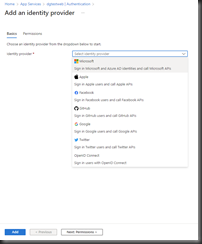
A new app will contain no Identity Providers. Click the [Add identity provider] button (Fig. 3) to open the "Add an identity provider" dialog, as shown in Fig. 4.
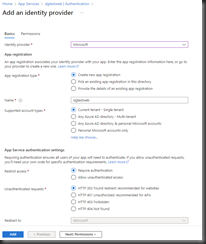
Completing this dialog will create a new App Registration in Azure Active Directory. From the "Identity provider" dropdown, select "Microsoft". The rest of the dialog will display prompts related to this provider, as shown in Fig. 5.
At the "App registration type" prompt, select the "Create new app registration" radio button.
At the "Name" prompt, enter a unique name for the app registration. This will default to the name of your web app.
At the "Supported account types" prompt, you can choose to restrict access to only accounts in the current Active Directory tenant, to accounts in this and other tenants, and/or to personal accounts registered with Active Directory.
At the "Restrict access" prompt, select the "Require authentication" radio button.
The "Unauthenticated requests" prompt allows you to select the HTTP response returned when a user fails to authenticate. Most of these are appropriate for APIs. For a website, select the "HTTP 302" radio button.
Click the [Add] button to create a new App Registration in Azure Active Directory and return to the "Authentication" blade, as shown in Fig. 6.
You should now see your newly created Identity Provider listed.
Grant access to roles
After registering your application, the next step is to grant access to specific users or roles within your app. By default, each App Service contains a couple of dozen roles. Adding an account to a role permits them to perform certain activities, such as viewing or updating your site.
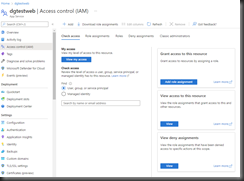
To assign an account to a role, click the [Access control (IAM)] button (Fig. 7) in the left menu to open the "Access control (IAM)" blade, as shown in Fig. 8.
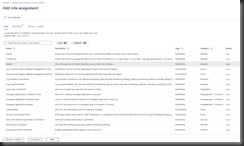
On the "Access control (IAM)" blade, click the [Add role assignment] button (Fig. 9) to open the "Add role assignment" page, as shown in Fig. 10.
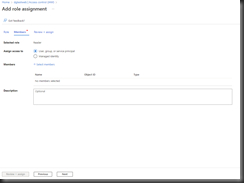
On the "Role" tab, select the "Reader" role; then, click the [Next] button to advance to the "Members" tab, as shown in Fig. 11.
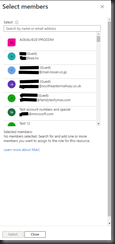
Click the "Select members" link (Fig. 12) to open the "Select members" dialog, as shown in Fig. 13.
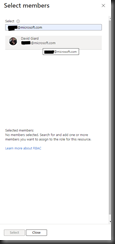
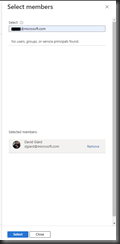
Search for an Active Directory account, as shown in Fig. 14 and 15.
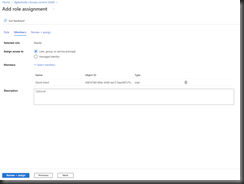
Click the [Select] button to add this account to the "Reader" role. You will return to the "Add role assignment" page, as shown in Fig. 16. The account will now be listed under "Members".
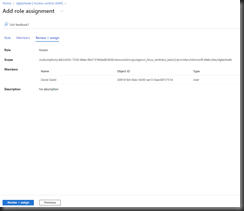
Click the [Review + assign] button to advance to the "Review + assign" tab, as shown in Fig. 17.
Click the [Review + assign] button to save your changes.
Conclusion
In this article, you learned to configure Azure Active Directory as an Identity Provider for an Azure Web App. The steps above will create a new App Registration, which you can view from the "App Registration" blade of Azure Active Directory, as shown in Fig. 18.
You have the option to create and configure the App Registration yourself; but the steps describe here take care of much of the configuration for you.