Implementing Conditional Access Policies in Azure Active Directory
January 03, 2023 3:08 Comments [0]Overview
Sometimes it makes sense to apply a security policy to every user in every context. But sometimes you may want to apply to only certain users accessing specific applications in specific ways. For example, you may want to block guest accounts from accessing SharePoint applications. Or you may want to require Multi-Factor Authentication for users in specific countries. Azure Active Directory Conditional Access allows you to implement such security policies.
Steps
To implement a Conditional access policy, log onto the Azure Portal as an Administrator; then search for Azure Active Directory, as shown in Fig. 1.
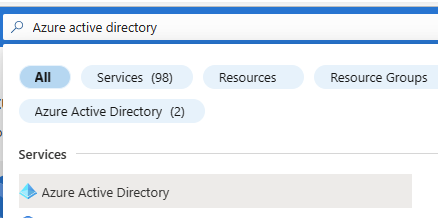
Fig. 1
The "Overview" blade of Azure Active Directory displays, as shown in Fig. 2.
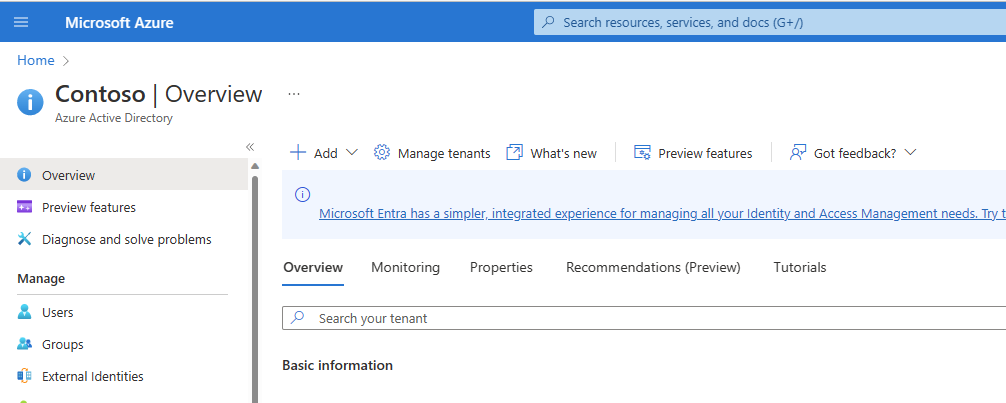
Fig. 2
In the left menu, click the [Security] button (Fig. 3) to open the "Security" blade, as shown in Fig. 4.

Fig. 3
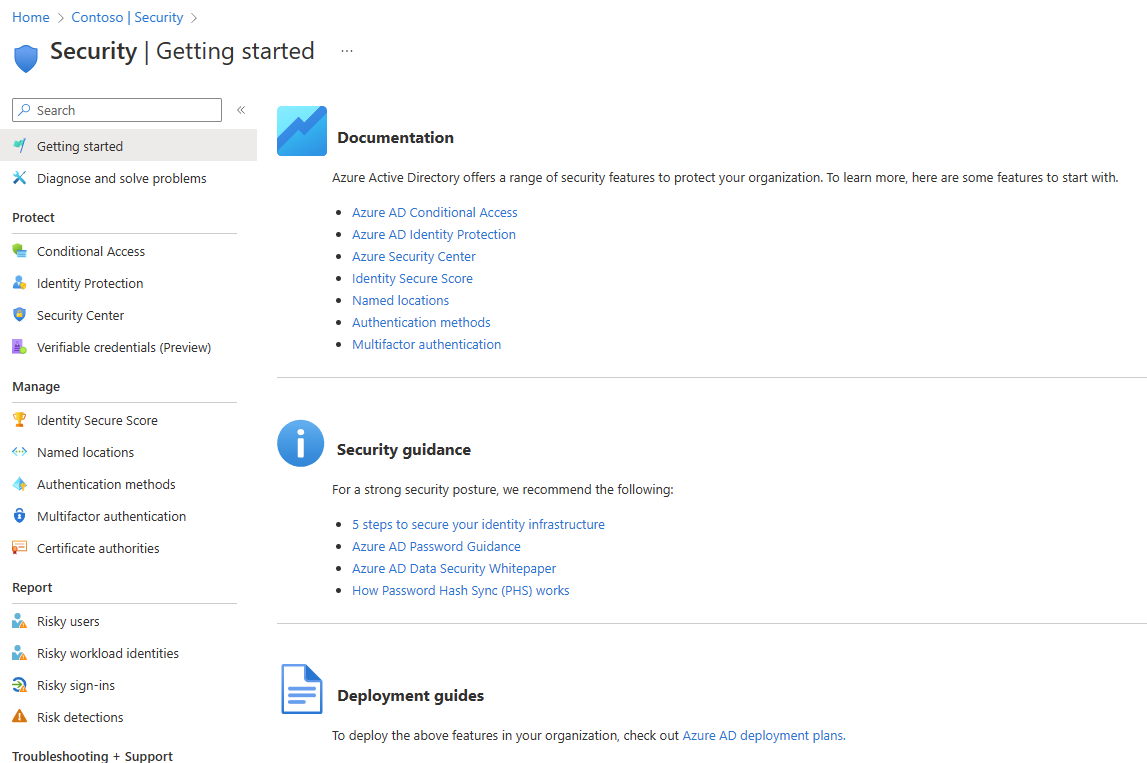
Fig. 4
In the "Protect" section of the left menu, click the [Conditional Access] button (Fig. 5) to open the "Conditional Access Policies" blade, as shown in Fig. 6.
Fig. 5
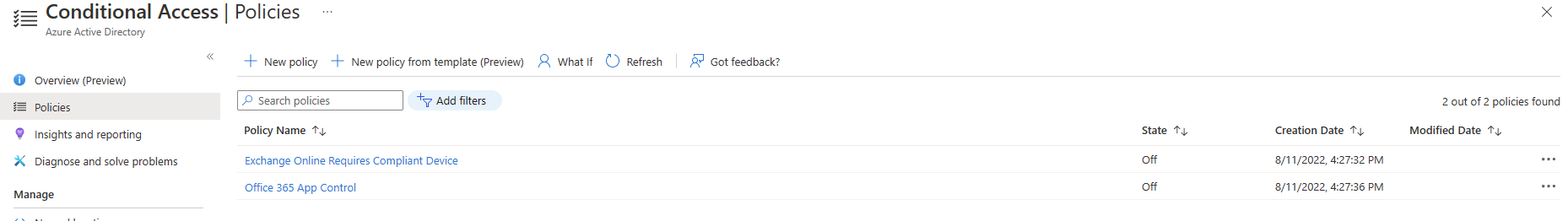
Fig. 6
To create a new Conditional Access policy, click the [New policy] button (Fig. 7) to display the "New Conditional Access policy" dialog, as shown in Fig. 8.
Fig. 7
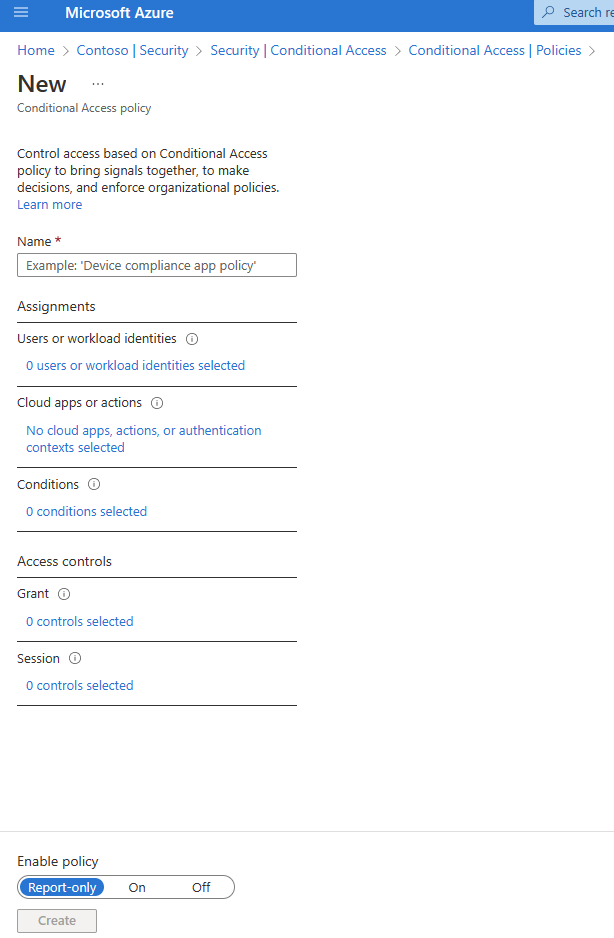
Fig. 8
At the "Name" field, enter a unique (to this AAD) name for this policy.
This dialog contains five sections. Clicking each of these prompts you for more information. You do not need to configure each section. I will explain each section below.
Users or Work identities
The "Users or Work Identities" section (Fig. 9) allows you to determine which users, groups, and roles are affected by this Conditional Access Policy.
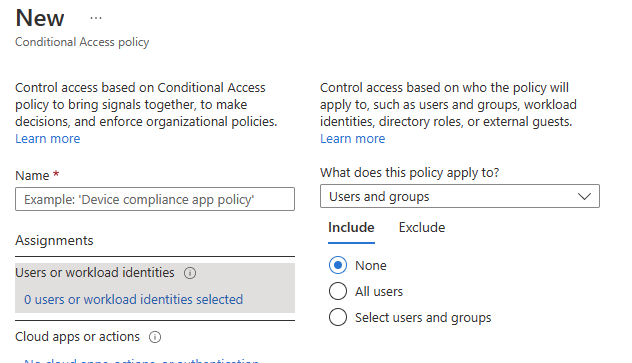
Fig. 9
By default, this criterion is ignored, but you can include all users or select specific users, roles, or groups. You can also specify that it applies to all users except those you exclude by clicking the "Exclude" tab and selecting users and/or groups to exclude.
Cloud apps or actions
The "Cloud apps or actions" section allows you to include or exclude this policy based on which apps are accessed or actions are taken. Fig. 10 shows the "Cloud apps" options, which allow you to Include or exclude specific applications.
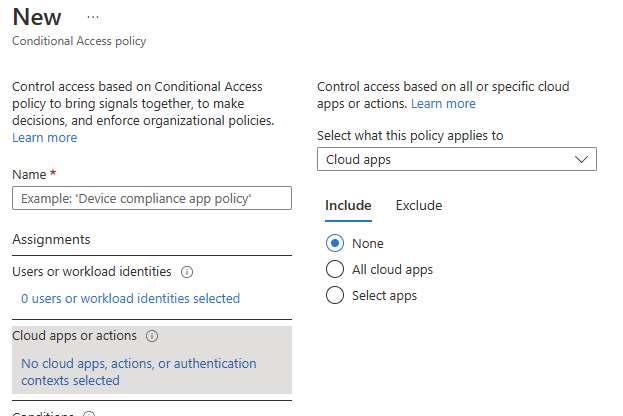
Fig. 10
Fig. 11 shows the "User actions" option, allowing you to apply this policy to when a user self-registers their security information or when they identify a device, such as a phone or laptop, to Active Directory.
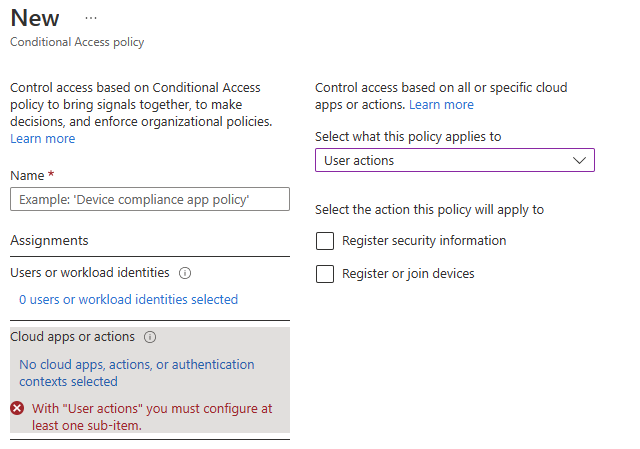
Fig. 11
Conditions
The "Conditions" section (Fig. 12) allows you to specify which conditions trigger the policy.
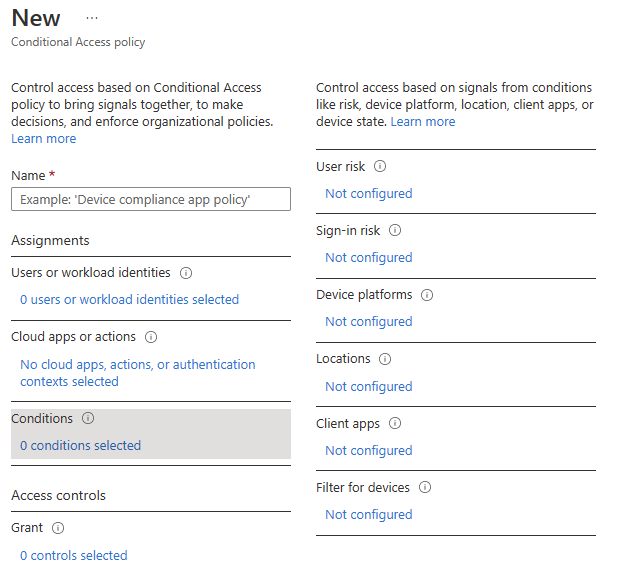
Fig. 12
Conditions are categorized by the following categories:
- User risk
- Sign-in risk
- Device platform
- Locations
- Client apps
- Filter for devices
User risk
This can include known leaked credentials or activity detected that is unusual for the current user
Sign-in risk
This an include users signing in from an unusual location or from two distant locations in a short period of time or from a suspicious IP address.
Device platform
You can specify policies based on the device used to log in. If you distrust Android security, you may want to force extra login policies when logging in with an Android device.
Locations
This allows you to apply policies when a user logs in from a specific location. For example, you may want to restrict users from logging in from Russia. Or you may want to require Multi-Factor Authentication when logging in from outside the United States.
Client apps
Here you can apply the policy based on the application the user is accessing. For example, you can apply different policies for browser apps than for rich client apps.
Filter for devices
This section lets you apply complex queries that identify properties of the device from which the user is accessing the system.
Grant
The "Grant" section (Fig. 13) specifies what happens if the user and client meet the criteria specified in the sections above.
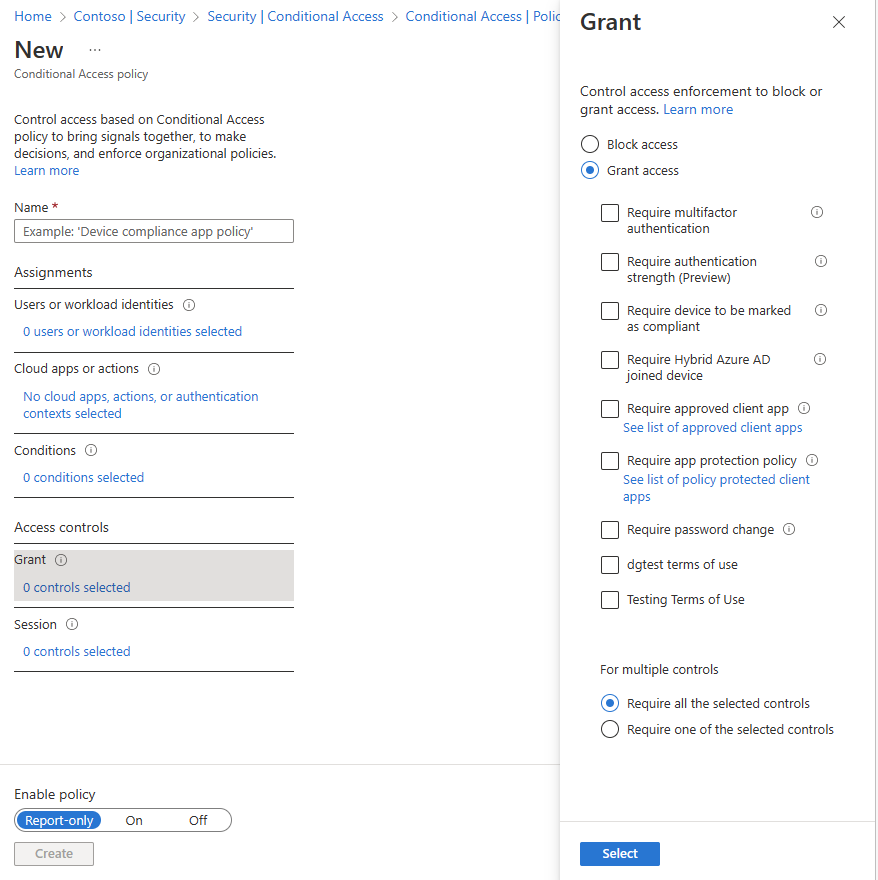
Fig. 13
You can choose to block access if they meet the criteria; or you can choose to grant access - but only if they perform some function, such as multifactor authentication or setting a strong password.
Session
If a Conditional Access Policy applies to a user and the user satisfies the login requirements, you can use the "Session" section (Fig. 14) to determine how long they remain signed in. A common use case is to check "sign-in frequency" and require the user to re-authenticate after a given amount of time.
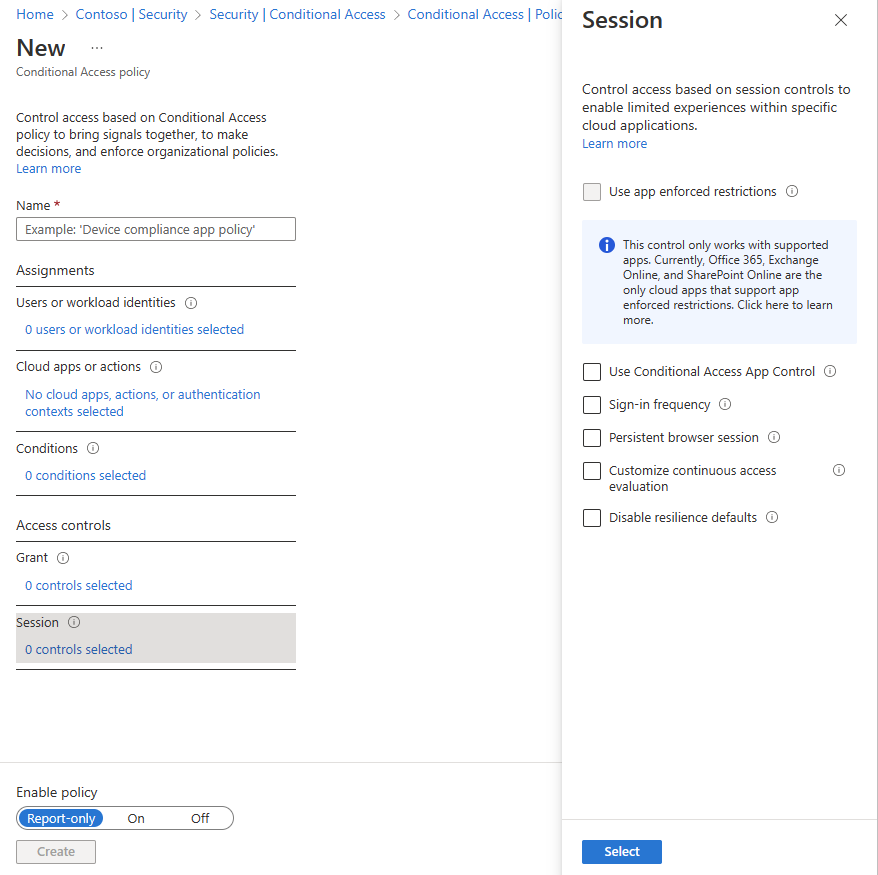
Fig. 14
Enable policy
At the bottom of the page
Conclusion
Conditional Access Policies are a powerful way to either block groups of users or to require additional barriers when users connect in potentialy unsafe ways. In this article, you learned how to configure Conditional Access Policies in Azure Active Directory.