Azure Storage Accounts allow you to store data in the cloud in a secure, scalable, and highly available way. A Storage Account provides storage of four broad categories of data objects: blobs, tables, queues, and files.
This article walks you through the process of creating an Azure Storage Account.
Navigate to the Azure Portal and log in.
Click the [Create a resource] button (Fig. 1) and search for "Storage Account," as shown in Fig. 2.

Fig. 1

Fig. 2
From the list of results, select the [Create] button in the "Storage Account" panel (Fig. 3) to expand the menu, and select the [Create] option, as shown in Fig. 4.

Fig. 3

Fig. 4
The "Create a Storage Account" dialog displays with the "Basics" tab selected, as shown in Fig. 5.

Fig. 5
At the "Subscription" dropdown, select the subscription in which you want to create this Storage Account. Many of you will have only one subscription, so you will not need to choose anything here.
At the "Resource group" field, select the resource group in which you want to create the Storage Account, or click the "Create new" link to create a new resource group in which to add the Storage Account. A resource group is a logical grouping of Azure resources you want to manage together.
At the "Storage account name" field, enter a unique name for this Storage Account.
At the "Region" dropdown, select an Azure region in which to create the Storage Account. Consider the location of the people and services that will be using the data in this account to minimize latency.
At the "Primary service" dropdown, select how you most often plan to use this account. Azure will optimize the account for this service. The options are:
- Azure Blob Storage or Azure Data Lake Storage Gen 2
- Azure Files
- Other (tables and queues)
At the "Performance" radio button, select "Premium" if you require high-speed data access. This selection will cost extra. Select "Standard" if you do not need low latency.
At the "Redundancy" dropdown, select the type of redundancy you would like for this service. Although all Azure Storage Accounts create multiple copies of your data, you can decide where that data is stored: in the same data center or in a different region. The options are listed in ascending order of protection and cost, with a description below each option.
Fig. 6 shows the "Advanced" tab. It is unnecessary to change anything on this tab, but it allows you to configure additional security on the account.

Fig. 6
Fig. 7 shows the "Networking" tab. Changing anything on this tab is unnecessary, but it allows you to restrict access to the account to specific networks and configure private endpoints.

Fig. 7
Fig. 8 shows the "Data protection" tab. It is unnecessary to change anything on this tab, but it allows you to configure the Storage Account to make it possible to roll back changes to your data.

Fig. 8
Fig. 9 shows the "Encryption" tab. It is unnecessary to change anything on this tab, but it allows you to configure what is encrypted and how to encrypt it.

Fig. 9
Fig. 10 shows the "Tags" tab. It is not necessary to change anything on this tab, but you can apply name-value pairs to this resource that you may use to filter or sort your reports.

Fig. 10
Fig. 11 shows the "Review + create" tab. If you made any errors, such as leaving a required field empty or selecting an inconsistent combination of options, these errors will be listed here, and you will need to correct them before you can proceed.

Fig. 11
After correcting any errors, click the [Create] button (Fig. 12) to start the creation of the Azure Storage Account.

Fig. 12
After a short time, a confirmation message similar to the one in Fig. 13 will display, indicating that the Storage Account has been created.
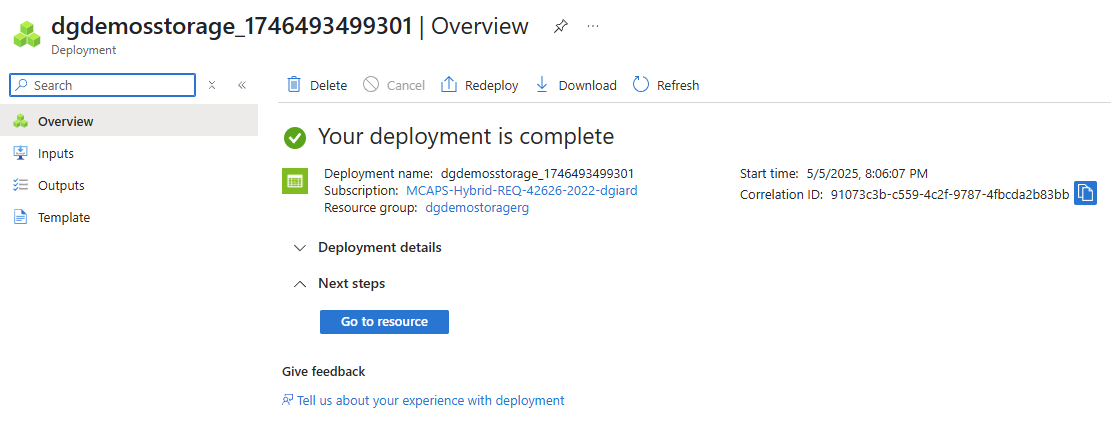
Fig. 13
Click the [Go to resource] button (Fig. 14) to show the "Overview" blade of the newly created Storage Account, as shown in Fig. 15.

Fig. 14

Fig. 15
This article showed you how to create an Azure Storage Account. I will show you how to add data and work with this account in future articles.
 I confess that I was not a fan of Alicia Keys before attending Thursday's production of "Hell's Kitchen" at Broadway's Shubert Theatre. I never disliked her music, but I was born too early to be her target audience, and I never caught up.
I confess that I was not a fan of Alicia Keys before attending Thursday's production of "Hell's Kitchen" at Broadway's Shubert Theatre. I never disliked her music, but I was born too early to be her target audience, and I never caught up.